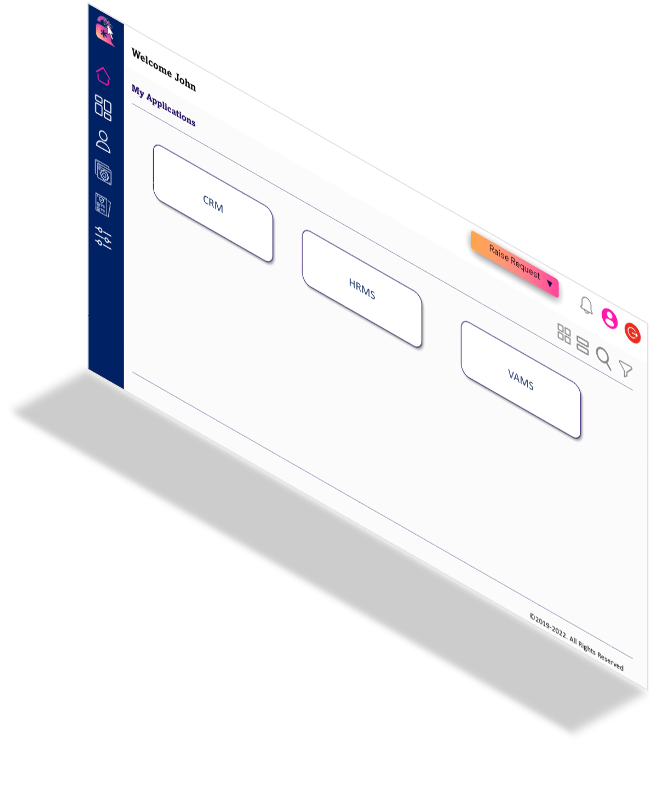
As organizations grow, one of the biggest IT challenges they face is how to best secure their environment & ensure that 100% employees follow the password policies. A-ZTSSO solution, ensures that companies can rest knowing that the right people have the right level of access. Even more, users can safely access all of their apps without needing to remember any passwords, from any device. Autharc SSO gives users a better experience by providing access to all IT systems needed with a username and password-less login mechanism. With its one step multi-factor authentication, it adds vital security functionality to your native and non-native software landscapes
Single-pane Zero Trust Gateway to Apps Autharc Zero Trust Single Sign-On
Deliver a smooth secure access user experience
Get Started